[ad_1]
The play-and-own mobile gaming platform GAMEE suffered an exploit of its GMEE token contracts on Polygon that led to the theft of 600 million GMEE tokens and left the crypto community pondering questions.
GAMEE Confirms $15M Exploit On Polygon
On January 22, GAMEE Token’s official X (formerly Twitter) account advised its users to refrain from engaging with the digital asset while their team investigated the GMEE token-related security comprise it had just suffered.
The GMEE token is an ERC-20 utility token “designed to be the currency of access, action, and governance within the GAMEE ecosystem,” as their website states.
🚨 $GMEE | URGENT
There has been a security incident involving the GMEE token. As a precautionary measure, we advise all users to refrain from engaging with $GMEE until further notice.
Our team is actively investigating the situation, and updates will be provided soon.
— GMEE Token (@GAMEEToken) January 22, 2024
Before the official announcement, crypto users quickly noticed the token’s sudden price crash and the transactions behind it. This left GAMEE users and the general crypto community wondering if an exploit had occurred.
In the early hours of January 23, GAMEE’s team returned to the X platform to explain what happened and the steps to come.
The thread explains that their preliminary investigation indicated that the GMEE token contracts on Polygon had been compromised via unauthorized GitLab access.
This compromise resulted in the theft of 600 million GMEE tokens worth approximately $15.28 million at the time of the exploit. The compromised tokens were immediately converted to ETH and MATIC and exchanged via various decentralized exchanges (DEXs) in the following hours, drastically impacting the GMEE token price.
The team behind GAMEE explained that after noticing the Polygon GMEE deployer address was compromised, they secured the token contract ownership and all associated contracts by transferring ownership to a “new secure address.”
The team also clarified that only proprietary team token reserves were affected, and the exploit did not affect assets owned by the community, as “GAMEE does not custody or manage any community-owned assets.”
GAMEE expressed its understanding of how the impact of the unauthorized transactions could have affected the GAMEE community, as it led to price volatility and limited use of the GMEE token while investigations were taking place.
The next steps for GAMEE will consist of an impacted user identification process to evaluate the best way to support the affected part of the community. Additionally, they plan to provide a real-time update on the details that further investigations will provide as an effort to keep trust and transparency.
Lastly, the user was advised to exercise caution “given the volatile market conditions and potential liquidity impacts driven by CEX measures.”
GMEE’s Violent Price Drop
Around the time of the exploit, the GMEE token had been trading at $0.02554112, according to CoinGecko’s data, and it had been previously sitting at the $0.027-$0.026 range throughout the weekend.
Shortly after the exploit, the prince crashed to $0.01155577, reaching its lowest point of $0.00897251 in the early hours of today.
It’s worth noting that many saw the price crash as a possibly once-in-a-lifetime opportunity to profit. Various users shared that they had bought the dip and even advised others to do it. One X user said, “One man’s trash is another man’s treasure.”
At writing time, the GMEE token trades at $0.016999, a 31.5% decline in the last 24 hours.
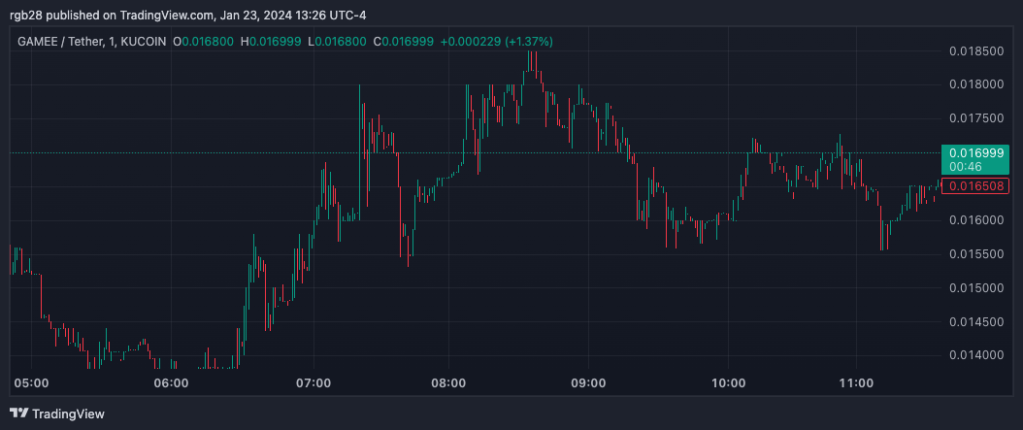
GAMEE is currently trading at $0.016999 in the hourly chat. Source: GMEEUSDT on TradingView.com
Featured Image from Unsplash.com, Chart from TradingView.com
Disclaimer: The article is provided for educational purposes only. It does not represent the opinions of NewsBTC on whether to buy, sell or hold any investments and naturally investing carries risks. You are advised to conduct your own research before making any investment decisions. Use information provided on this website entirely at your own risk.
[ad_2]
Source link